[Suspension of NBDC Human Database activity during the New Year Holidays] DBCLS will be closed for the New Year Holidays from December 27, 2025 (Sat) to January 5, 2026 (Mon).
After January 6 (JST), we will respond to requests or questions which are received during this period.
We sincerely apologize for any inconvenience this may cause and thank you for your kind understanding and cooperation.
We are currently receiving a large number of Applications for data submission, and the review process is taking longer than usual.
We sincerely apologize for the delay and kindly ask for your understanding.
When submitting an application, we would greatly appreciate it if you could allow sufficient time for the processing.
About NBDC Human Database
An enormous amount of human data is being generated with advances in next-generation sequencing and other analytical technologies. We therefore need rules and mechanisms for organizing and storing such data and for effectively utilizing them to make progress in the life sciences.
To promote sharing and utilization of human data while considering the protection of personal information, the Database Center for Life Science (DBCLS) of the Joint Support-Center for Data Science Research, Research Organization of Information and Systems (ROIS-DS) created a platform for sharing various data generated from human specimens, which are available for publicly access in cooperation with the DNA Data Bank of Japan![]() .
.
You can apply to use or submit human data through this website.
Violators of the guidelines who have not submitted a report on the deletion of Controlled-access data shall be disclosed here.
What's New
Policy_Japan Only
Data use is limited to Japan (JGAP000014)
Additionally, data use is limited to Japan.
Policy_hum0511
Data Sharing Policy for hum0511 (JGAP000013)
In addition to the NBDC policy,
Users shall not disclose variants or other genetic information attributable to individual samples when presenting analysis results that include this dataset in academic publications, conference presentations, or other forms of dissemination.
About Revision of “NBDC Guidelines for Human Data Sharing” and “NBDC Security Guidelines for Human Data”
About Revision of “NBDC Guidelines for Human Data Sharing” and “NBDC Security Guidelines for Human Data”
Department of NBDC Program (NBDC) of the Japan Science and Technology Agency (JST) partially revised “the NBDC Guidelines for Human Data Sharing” and “the NBDC Security Guidelines for Human Data” and the revised guidelines come into effect on April 1, 2022.
- Purpose of Revision
Revisions have been made to clarify the items to be complied with by the users of the "Registered-access Data," which were newly established at the time of the last revision, and to reflect the revisions of research ethics guidelines and laws related to the protection of personal information, which constitute the legal basis and guidelines for the "NBDC Guidelines for Human Data Sharing" and the "NBDC Security Guidelines for Human Data." These revisions and additions have been reviewed and approved by the Data-Sharing Subcommittee, Steering Committee of the NBDC and the Steering Committee of the NBDC, and will come into effect on April 1, 2022.
- Revision Points
- (1) Clarification of specific items to be complied with by "registered-access data" users
The "NBDC Guidelines for Human Data Sharing" and the "NBDC Security Guidelines for Human Data (for Data Users)" have been revised to specifically present the items to be complied with when using the "registered-access data."
- (2) Revisions due to implementation of new research ethics guidelines
The "Ethical Guidelines for Medical and Biological Research Involving Human Subjects" came into effect on June 30, 2021, and the "Ethical Guidelines for Human Genome/Gene Analysis Research" and the "Ethical Guidelines for Medical and Health Research Involving Human Subjects" were abolished on the same day. In line with the above, the revisions in related descriptions in the Guidelines have been revised. In addition, the following two items have been added regarding the provision of information to third parties in foreign countries (outside Japan), which is one of the revisions to the Act on the Protection of Personal Information, as amended in 2020.
-
- (i) Sample statement in the explanatory document for obtaining informed consent
- An increasing number of journals are requiring that the data on which articles are based be registered in public databases and shared when the articles comprising research results are published. Since foreign third parties may be involved in data sharing through public databases, a sample statement has been provided for providing research participants with a necessary explanation of how data registered in public databases will be shared.
- (ii) Description of country and state name
- Information on data users is posted on each Research page of the NBDC Human Database. Revisions are made to add the name of the country and state to the information on data users, to clearly indicate which country and state researchers are using the data.
- (3) Other amendments
For clarification, the subjects for which redistribution prohibition is imposed and the procedures for storing and distributing secondary data have been added. In addition, the data that should be deleted at the end of data use by data users who used the off-premise server has been clarified.
- (1) Clarification of specific items to be complied with by "registered-access data" users
- Contact information for the operation of the Guidelines
We accept inquiries about the Guidelines from the NBDC Human Database Inquiry Form at the following URL and respond after consultation as appropriate. In addition, we provide information on the NBDC Human Database website by preparing and posting a list of questions and answers which includes representative answers to inquiries.
The NBDC Guidelines for Human Data sharing
The NBDC Security Guidelines for Human Data (For Data Users)
The NBDC Security Guidelines for Human Data (For Data Submitters)
The NBDC Data Sharing Subcommittee Office and The NBDC Human Data Review Board Office
Address: 5-3, Yonban-cho, Chiyoda-ku, Tokyo, 102-8666
Tel : +81-3-5214-8491
Fax : +81-3-5214-8470
Inquiry Form: https://humandbs.biosciencedbc.jp/contact-us
NBDC Guidelines for Human Data Sharing ver. 7.0
Click to Latest version.
April 1, 2022
Ver. 7.0
Introduction
An enormous amount of human data is being generated as advancements are made in analytical techniques such as next-generation sequencing. Rules and systems are therefore needed for storing such data in an organized manner and for effectively utilizing them to make progress in life sciences and to improve public health.
To promote sharing and utilization of human data for the above purposes while considering protection of personal information, the Department of NBDC Program (hereinafter, NBDC) of the Japan Science and Technology Agency (JST) established a platform for sharing various human-related data (hereinafter, the NBDC Human Database) and developed rules and guidelines (hereinafter, the Guidelines) for operating it.
The Guidelines are designed to be applied to human data in general that were generated using public funds. Because the relevant guidelines, policies, and laws are amended as necessary to appropriately reflect, the consistency has not been verified between the Guidelines and all of them. In addition, global trends concerning life science data as well as the attitude of the general public toward scientific data are expected to change. To respond to such changes, the Guidelines are reviewed and revised whenever it becomes necessary.
Contact information:
For information on the Guidelines
NBDC Data Sharing Subcommittee Office
https://humandbs.biosciencedbc.jp/en/contact-us
For information on data use or data submission for the NBDC Human Database
NBDC Human Data Review Board Office
https://humandbs.biosciencedbc.jp/en/contact-us
Contents
- Principles
- Definitions
- Acceptable Data
- Data Submission to the NBDC Human Database
- Using Data in the NBDC Human Database
- Procedure for Revising the Guidelines
- Other Topics
1. Principles
- The NBDC Human Database is administered toward the following goals.
- 1: Collecting human data generated using public funds as much as possible
- 2: Promoting wide sharing of collected data
- 3: Respecting to the greatest extent possible the rights of individuals who are research subjects
- The NBDC performs the following in administering the NBDC Human Database.
- Maintaining the Guidelines and reexamining them as the need arises
- Reviewing applications for data use and data submission
- Maintaining a means to access data, e.g., website maintenance
2. Definitions
- Human data
- Data generated as a result of a study using human-derived specimens. Such data include genomic and genetic information, clinical information, image information, and so on.
- Public funds/grants
- Funds provided by national and local governments, incorporated administrative agencies, and equivalent organizations.
- Research subject
- A person who has provided a sample such as his/her own tissue, blood, and urine, or his/her own data, for an activity such as a study or research project.
- Data submitter
- A principal investigator (hereinafter, PI), who provides human data to the NBDC Human Database.
- Data user
- A PI and his/her research collaborators, who use human data from the NBDC Human Database. Research collaborators must belong to the same organization as the PI, and have been listed as data users in the application for data use filed by the PI.
- Principal investigator (PI)
- An investigator responsible for the study. (The investigator who submitted a research protocol to the Ethical Review Committee of his/her affiliated or an equivalent organization and obtained its approval, or a research collaborator who is listed in the application for the ethical review of the study.)
- Unrestricted-access data
- Data available for use without any access restrictions. Examples include statistical data or reference data previously disclosed in a published paper.
- Data accessible to registered users (Registered-access data)
- Data available to investigators who have been approved by the NBDC Human Data Review Board for the usage of controlled-access data, during the data usage period. Included are statistical data created by processing each dataset registered as the controlled-access data at the NBDC databases.
- Controlled-access data
- Data available only to investigators for use for research purposes. The access-granted investigators must have research experience in related studies and can use the data for their studies, after clarifying information such as the purpose of data use and data users. For use, approval is required at the review by the NBDC Human Data Review Board. Controlled-access data include individual data like nucleotide sequence data containing output from next-generation sequencer, genome-wide variant data, image information, answers to a questionnaire, and so on.
- Data for future release
- Data that are planned to be released as unrestricted-access data or controlled-access data after the data submitter makes the results public, e.g., by publication of a paper, acquisition of intellectual property rights, and so on.
- Secondary data
- Data that are processed not to be able to restore primary data (controlled-access data shared via NBDC human databases).
- Available server outside of affiliated organization (“Off-premise-server”)
- A server that is not owned by data users’ affiliated organization and that is available to the data users to store and/or process controlled-access data, which “off-premise-server” has a computing environment for analyzing human data. The computing environment is owned by an organization that has concluded with JST a memorandum concerning operation including the compliance with the NBDC Security Guidelines for Human Data (for Database Center Operation Managers and “Off-Premise-Server” Operation Managers). In addition, and measures necessary for high level (Type II) security are being implemented in the “off-premise-server.”
(“Off-premise-server”: https://humandbs.biosciencedbc.jp/en/off-premise-server)
- A server that is not owned by data users’ affiliated organization and that is available to the data users to store and/or process controlled-access data, which “off-premise-server” has a computing environment for analyzing human data. The computing environment is owned by an organization that has concluded with JST a memorandum concerning operation including the compliance with the NBDC Security Guidelines for Human Data (for Database Center Operation Managers and “Off-Premise-Server” Operation Managers). In addition, and measures necessary for high level (Type II) security are being implemented in the “off-premise-server.”
- Entrustee
- An entity or person who is entrusted by a data user to perform only a part of the work related to a research, such as storage of data or data processing, under the supervision of the data user. When entrusting the work to an entrustee located overseas (outside Japan), the PI at the time of application for data use must implement ethical procedures such as receiving appropriate consent from the research participants and others.
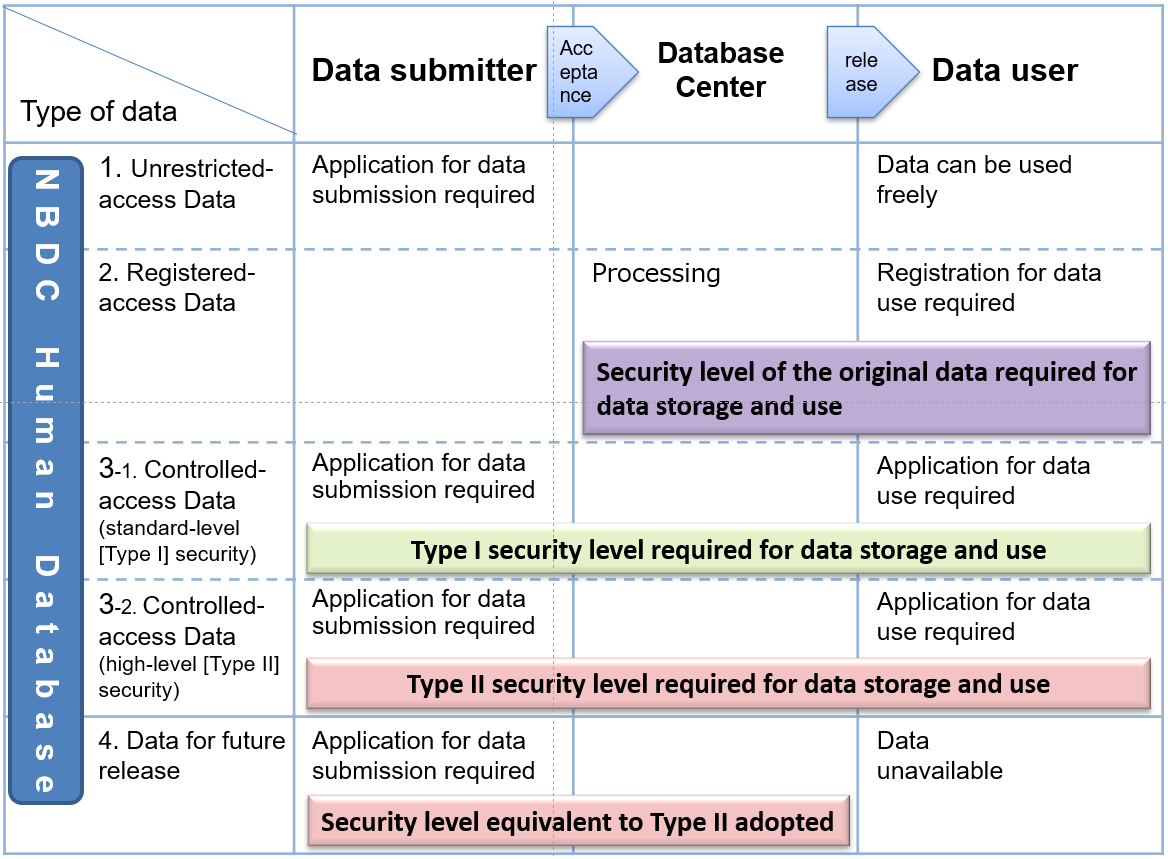
3. Acceptable Data
Overview of acceptable data
The NBDC Human Database accepts a wide range of human data generated in projects that receive public funds. Because this database is aimed for data utilization among many investigators, it cannot be used as a repository for data shared among only limited collaborators of a research group or a consortium. Therefore, data that are provided for such a purpose cannot be accepted.
Data are classified into the following four types according to the state of data release and the level of access restriction (see the figure below).
- Unrestricted-access data
- Registered-access data
- Controlled-access data
- Data for future release
The NBDC Human Database accepts: 1) unrestricted-access data, 3) controlled-access data, and 4) data for future release. The NBDC Human Database accepts only these data that have been pseudonymized by the data submitter by replacing a part or all of personal information which enable identification of a specific individual (including a specific deceased individual) with descriptions, e.g., a code or number which is unrelated to the specific individual, and then by assigning another code or number again. Registered-access data (2.) are data created by the database center from the controlled-access data through processing for the purpose of promoting data use.
4. Data Submission to the NBDC Human Database
4.1 Rights of the Data Submitters
- Data submitters can designate data use restrictions that conform to those specified in the informed consent form (e.g., limitation on the scope of diseases for data use).
- Data submitters, while being asked to agree with prompt release of their data, can request that the data be designated as data for future release for the purpose of publication of research results, acquisition of intellectual property rights, etc. It is noted, however, the release may be delayed only for a term reasonable and necessary for such purposes. Concrete details are determined in a consultation with the NBDC Human Data Review Board.
4.2 Responsibilities of Data Submitters
- The data submitter must obtain permission from the head of his/her affiliated organization after taking the following steps: (1) Explain the required descriptions in the “Examples of Content for Informed Consent Forms” (shown below) to a research subject from whom the human data are collected; (2) Obtain written consent from the research subject regarding submission of the data to databases and sharing of the data by domestic and/or foreign investigators; and (3) Obtain approval regarding such data submission and data sharing from the Ethical Review Committee of the affiliated or an equivalent organization. However, if the data submission and data sharing were approved for the entire research project after an ethical review conducted at the start point of the project, then another review is not required.
- When the data submitter provides data to the NBDC human database collected from specimens, e.g., human biological specimens, diagnostic specimens, that were obtained without prior intention to submit such data to databases (e.g., in cases where the informed consent form does not refer to data submission or data sharing), the data submitter must follow procedures that conform to the ethical guidelines that must be complied with in conducting the research (for example, the data submitter obtain re-consent. Alternatively, if it is difficult to do re-consent, he/she must ensure information disclosure and opportunities of rejections (opt-out), and obtain permission from the head of his/her affiliated organization after obtaining approval of the Ethical Review Committee of the affiliated or an equivalent organization).
- When the data submitter provides data that is clearly not the subject of "Ethical Guidelines for Medical and Biological Research Involving Human Subjects" *[1] to the NBDC Human Database, the data submitter must submit a "statement requesting a simplified review of an application for data submission" (in an arbitrary format) signed by the PI (see example). Submission of this statement can be a substitute for submission of documents concerning ethics review of the affiliated organization (e.g., research protocol, informed consent form, and notice of approval).
*[1]: In "Ethical Guidelines for Medical and Biological Research Involving Human Subjects", specimens and information, the value of which has already been established academically, widely utilized in research and generally available. - While the NBDC Human Data Review Board reviews the descriptions of the informed consent form submitted at the time of application for data submission in terms of the consistency with the restrictions on data use, the data submitter is responsible for ensuring that the data are provided in accordance with the conditions of the consent.
- The data submitter must provide data according to the content of the "application form for submitting data" to the NBDC.
- The data submitter must confirm that the data to be submitted have been pseudonymized by replacing a part or all of personal information which enables identification of a specific individual (including a specific deceased individual) with descriptions, e.g., a code or number which is unrelated to the specific individual and further by assigning another code or number. In case of withdrawal of consent, in order to delete the data derived from the corresponding research subject, in principle, the data submitter must keep the decoding index.
- After selecting the type of data such as unrestricted-access data, controlled-access data, or so on based on consultation with the NBDC Human Data Review Board, the data submitter must provide the NBDC with the data along with any necessary accompanying data (e.g., metadata that explain the main data, as well as information needed for quality control). In addition, for controlled-access data, the data submitter must designate an appropriate security level (Type I or Type II) based on consultation with the NBDC Human Data Review Board.
- In case the data provided by the data submitter is found to be data that violate the NBDC Human Data Sharing Guidelines etc. or found to be data that contain a defect (including hidden defects) intentionally or with negligence, the NBDC will suspend publication of the provided data and delete the data. The data submitter must re-provide the data within a certain period of time after fixing data and/or necessary procedures. If re-provided is not done, the NBDC will cancel the accession number for the data.
- When there is a rejection by opt-out or a withdrawal of consent from a research subject from whom the data provided to the NBDC Human Database were derived, the data submitter must cooperate in the disposal of the data in order to avoid subsequent data use.
- The data submitter shall consent to the processing of the data conducted by the NBDC and the DDBJ Center for the purpose of improving the convenience of data users (creation of statistical data for the purpose of publishing an overview of the data, and creation of data, such as alignment data, variant call data, and statistical data processed by a specific analysis pipeline, that can be used by a data user who has been approved for data use by the NBDC Human Data Review Board if the user so desires).
In case the data submitter provided human data in violation of the NBDC Human Data Sharing Guidelines etc., or provided human data that contain a defect (including hidden defects) intentionally or with negligence, the NBDC may take one or more further actions such as reporting of the fact to the head of the organization to which the data submitter belongs, announcing of the fact on the website etc., and so on. Besides, the NBDC may seek compensation from the data submitter, if the NBDC determines that due to these reasons it has suffered damages such as inability of operation of “the NBDC Human Database” as stated in the section “1. Principles.”
Examples of Content for Informed Consent Forms
Informed Consent Forms
-
Registration to a database and sharing of research data among many investigators internationally.
- Sample statement: Since the data obtained for this study are also important for other studies which contribute to improved public health, they will be submitted to a public database or the database managed by the Department of NBDC Program (hereinafter, NBDC) of the Japan Science and Technology Agency and will be shared with many investigators internationally.
-
Use by a third party in a foreign country (outside Japan).
- Sample statement: It is unknown at this time which countries’ investigators will use the data in the future. However, investigators from any country are required to use the data in accordance with the guidelines of the database that are developed in accordance with the laws and guidelines in Japan.
-
Description of the NBDC
- Sample statement: Aiming for rapid advancement in research, the Department of NBDC Program (hereinafter, NBDC) of the Japan Science and Technology Agency conducts projects in order for broad sharing of various research data and operates public databases that store data obtained from various studies. The NBDC Human Database, one of the databases operated by the NBDC, aims for rapid development of medical research and others by widely sharing various data on humans while paying attention to the protection of personal information and making full use of valuable data including those from this (our) research. For that reason, we are also promoting not only research use in domestic research institutions but also the use of data for research in private companies such as pharmaceuticals and overseas institutions that contribute to academic research or public health improvement. In the NBDC Human Database, data are managed and released based on strict guidelines that conform to Japanese laws, regulations, and so on. For details, please see the Life Science Database Integration Project website (https://biosciencedbc.jp/en/).
-
The necessity and importance of data sharing
- Sample statement: The sharing of research data with other domestic and/or foreign investigators through a database can help advance related studies overall and can aid in the development of new technologies. Data sharing may contribute to the elucidation of causes of diseases and the development of new treatments and prevention methods, which have not been enabled.
-
Data released to the public
- Sample statement: When data obtained from research are released from the database, the access level (controlled-access or unrestricted-access) differs depending on the type of data. Aggregated information, e.g., frequency data/statistical data, that does not lead to the identification of individuals are handled as unrestricted-access data and used by many unspecified persons. The genetic information of individuals is handled as controlled-access data and used by researchers approved for data use after passing through a review on the validity of scientific viewpoint and research system.
-
Impossibility to remove data
- Sample statement: When research results have been published in a paper or at an academic conference, even if the consent is withdrawn, the content published in the paper or the conference cannot be withdrawn. In addition, even when data for each individual are published from the public database, your data may not be deleted if your data cannot be identified.
4.3 Procedure for Data Submission to NBDC Human Database
- The data submitter confirms that the responsibilities listed in the above section “4.2 Responsibilities of Data Submitters” are fulfilled.
- The data submitter consults and agrees with the NBDC Human Data Review Board Office, with regard to the data classification (unrestricted-access data or controlled-access data), the timing of the release in the case of data for future release, and so on.
- The data submitter applies for data submission in accordance with the procedure for data submission application. At the time of application, a copy of the research protocol (the application form for ethical review), a copy of the ethical review approval notification, and the informed consent form must be attached. If, however, data submission and data sharing have been approved by an ethical review or equivalent examination held at the beginning of the entire research project, a document indicating that fact may be used instead of a copy of the approval notification.
- The NBDC Human Data Review Board decides whether the data can be accepted.
- When the data submission application is approved, the data submitter prepares the data set to be provided (unrestricted-access data and/or controlled-access data).
- The data submitter sends the data with the required accompanying data as instructed by the NBDC.
- Changes to data, such as those due to updating or reclassifying the data, are made as the need arises based on consultation between the data submitter and the NBDC Human Data Review Board Office.
5. Using Data in the NBDC Human Database
5.1 Eligibility for Data Use
5.1.1 Unrestricted-access data
Anyone can use unrestricted-access data.
5.1.2 Registered-access data
Data are available to investigators during the data usage period who have been approved by the NBDC Human Data Review Board for the usage of controlled-access data. At the time of registration, the investigator needs to present an e-mail address issued by the organization to which he/she belongs.
- An investigator who has research experience (one who belongs to a university, public research institute, private-sector company, or the like, and who has research experience in conducting relevant studies). The use is limited to academic research or research that contributes to the improvement of public health.
5.1.3 Controlled-access Data
An investigator can apply for data use as the PI if he/she satisfies the data user requirements indicated in the limitation added for each data set. When applying for data use, the investigator must present the mail address issued by his/her affiliated organization.
- An investigator who has research experience in relevant studies (one who belongs to a university, public research institute, private-sector company, or the like and who has research experience in conducting relevant studies). The use is limited to academic research or research that contributes to the improvement of public health. At the time of application, publications related to the data that the investigator plans to use must be presented.
5.2 Rights of Data Users
5.2.1 Unrestricted-access data
- Data users can freely make the result of the study for which data from the NBDC Human Database are used public, as long as the responsibilities of data users and the limitation added for each data set are fulfilled.
- Data users can freely acquire intellectual property rights based on the result of the study for which data from the NBDC Human Database are used, as long as the responsibilities of data users and the limitation added for each data set are fulfilled.
5.2.2 Registered-access Data
- Data users who have completed the registration for registered-access data use can view the data.
5.2.3 Controlled-access Data
- Data users can freely make the result of the study for which data from the NBDC Human Database are used public, as long as the responsibilities of data users and the limitation added for each data set are fulfilled.
- Data users can freely acquire intellectual property rights based on the result of the study for which data from the NBDC Human Database are used, as long as the responsibilities of data users and the limitation added for each data set are fulfilled.
- Data users can download, store, and use the data from the database center in the designated area of an “off-premise-server,” in addition to the data server connected to the affiliated organization LAN.
- Data users can use the data processed by the NBDC and the DDBJ Center (data such as alignment data, variant call data, and statistical data, processed by a specific analysis pipeline).
5.3 Responsibilities of Data Users
5.3.1 Unrestricted-access data
- In using data, the data user must utilize the data with his/her own responsibility and evaluation of the quality, content, and scientific validity of the data.
- The data user must comply with the following rules for the data obtained from the NBDC Human Database as well as any data derived therefrom.
Basic rules to be complied with in using data
- The use of data is limited to research and/or development purposes only.
- The use of data for weapons development or military applications is prohibited.
- Identification of individuals is prohibited.
- The latest data should be downloaded and used.
- When the research results including data downloaded from the NBDC Human Databases (the DDBJ Sequence Read Archive, the NBDC Human data Archive, the Genomic Expression Archive, and so on) are made public in a publication or a presentation, the data user must state the accession number of the data set used. In addition, a statement such as the following** must be included as references to the paper in which the data set was originally reported, or as acknowledgments.
** Example of acknowledgment
(A part of) The data used for this research was originally obtained by AAAA research project/group led by Prof. /Dr. BBBB and available at the website of the NBDC Human Database (https://biosciencedbc.jp/en/) of the Japan Science and Technology Agency (JST).
5.3.2 Registered-access Data
- In using data, the data user must utilize the data with his/her own responsibility and evaluation of the quality, content, and scientific validity of the data.
- When conducting research that uses registered-access data, it is necessary to apply for the use of the original data and receive approval from the NBDC Human Data Review Board.
- The data user must ensure that no one other than the person who has completed the registration to use the registered-access data may view the registered-access data.
- When citing registered-access data in a publication or the like, the data user must state the accession number of the data set being cited.
5.3.3 Controlled-access Data
- In using data, the data user must utilize the data with his/her own responsibility and evaluation of the quality, content, and scientific validity of the data.
- The data user must take full responsibility (including responsibilities to third parties) for using data. The data user should understand that his/her responsibility will be extended to the head of his/her affiliated organization in case any problem occurs in data management and handling.
- When using controlled-access data contained in the NBDC Human Database, the data user must comply with the “Ethical Guidelines for Medical and Biological Research Involving Human Subjects” in Japan. That is, among others, before carrying out any medical or biological research involving human subjects using data obtained from the NBDC Human Database, the data user must prepare the research protocol, go through a review by an Ethical Review Committee of his/her affiliated or an equivalent organization, and obtain approval therefrom and authorization from the head of his/her affiliated organization.
- The data user must comply with the following rules for the data obtained from the NBDC Human Database as well as any data derived therefrom.
Basic rules to be complied with in using data
- The data users must be limited. (Access is granted only to the PI and his/her research collaborators who belong to the same organization as the PI.)
- The purpose of data use must be explicitly stated.
- The use of data for purposes other than those stated in the application is prohibited.
- The use of data is limited to research and/or development purposes only.
- The use of data for weapons development or military applications is prohibited.
- Identification of individuals is prohibited.
- Redistribution of data is prohibited. (Distribution of processed data with no or very low personal identifiability or primary data recoverability does not constitute redistribution subject to prohibition. However, in principle, an application for retention of secondary data or distribution of processed data is required.)
- The data user must securely handle data, complying with the NBDC Security Guidelines for Human Data (for Data Users). Attention should be paid to the fact that the security level to be maintained varies for different data.* The data user must accept an audit conducted by the NBDC Human Data Review Board or a third party commissioned by the NBDC with regard to the state of implementation of security measures.
* Security levels:
Standard-level (Type I) security is required in principle, but high-level (Type II) security may be required based on consultation between the data submitter and the NBDC Human Data Review Board. For details on Type I and Type II security, see the NBDC Security Guidelines for Human Data (for Data Users).
- The data user must establish a security control system depending on the security level (Type I, Type II) and submit "Checklist for the NBDC Security Guidelines for Human Data" to the NBDC Human Data Review Board Office in order to demonstrate that the system conforms to the standards set forth by the NBDC.
- The data user must follow the terms of each ”off-premise-server” use in addition to the NBDC Human Data Sharing Guidelines and the NBDC Human Data Security Guidelines when using the ”off-premise-server” for his/her data use.
- Should a security incident such as data breach occur, the data user must immediately disconnect relevant devices from the network and report the incident to the NBDC. The data user must promptly implement post-incident measures, following instructions from the NBDC. When the “off-premise-server” is used, the data user must immediately take measures according to the terms of use etc.
- When the data user is informed of withdrawal of consent, rejection by opt-out in relation to the data that he/she downloaded from the NBDC Human Database and is using, the data user must not use the relevant data thereafter.
- When finished with using data, the data user must delete all data obtained from the NBDC Human Database (whole data, or any part of the data stored. When the off-premise-server is used, all the data stored on the off-premise-server, including backup data on the off-premise-server.) and all the data that can restore the data in accordance with the NBDC Security Guidelines for Human Data (for backup data on the off-premise-server, confirm when the data will be deleted), and report on the use (and deletion) of the data, using "Report on the Use (and Deletion) of Controlled-access data". With regard to keeping secondary data (e.g., results of calculations or statistical analyses based on controlled-access data) or distribution of processed data with no or very low personal identifiability or primary data recoverability, see the section on the procedure for using controlled-access data (“5.4 Procedure for Data Use”; Subsection “5.4.3 Controlled-access Data”). When the secondary data contains genetic data, the data must be properly managed as personal information and redistribution of the secondary data is prohibited.
- When the research results including data downloaded from the NBDC Human Databases (the Japanese Genotype-phenotype Archive, the NBDC Human data Archive, and so on) are made public in a publication or a presentation, the data user must state the accession number of the data set used. In addition, a statement such as the following** must be included as a reference to the paper in which the data set was originally reported, or as acknowledgment.
** Example of acknowledgment
(A part of) The data used for this research was originally obtained by AAAA research project/group led by Prof. /Dr. BBBB and available at the website of the NBDC Human Database (https://biosciencedbc.jp/en/) of the Japan Science and Technology Agency (JST).
When the service of JGA was used, it is desirable to refer to the following paper: Nucleic Acids Res. 2015, 43 Database issue: D18-22.
- The data user agrees that the NBDC may make certain statistical information or information about data user public upon release of the utilization conditions of the NBDC Human Database. Such information on data user that may be laid open includes the Dataset ID of the data used, the data user’s name, the data user's affiliated organization, country and state, the period of the data use, and the research title.
- The data user agrees that, for the purpose of release of the utilization conditions of the NBDC Human Database, the NBDC holds information on data usage, including information on the data users that is obtained from the time of application to the time of reporting the end of data use and information gathered at the time of incidents.
In case the data user used human data in violation of the NBDC Human Data Sharing Guidelines etc., or caused information leakage etc. in using data intentionally or with negligence, the NBDC may take one or more further actions such as rescinding of permission for data use, reporting of the fact to the head of the organization to which the data user belongs, announcing of the fact on the website etc., and so on. Besides, the NBDC may seek compensation from the data user, if the NBDC determines that due to these reasons it has suffered damages such as inability of operation of “the NBDC Human Database” as stated in the section “1. Principles.” The above conditions are applied to not only the PI but also his/her research collaborators. The PI is responsible for his/her research collaborators' compliance with the Guidelines (this document) and the NBDC Security Guidelines for Human Data (for Data Users).
5.4 Procedure for Data Use
5.4.1 Unrestricted-access data
The data user can freely use unrestricted-access data available from the website for the NBDC Human Database (https://humandbs.biosciencedbc.jp/en/), as permitted under laws and regulations.
5.4.2 Registered-access Data
- Among investigators who have been approved by the NBDC Human Data Review Board and are during the data use period, those who wish to use the registered-access data register their investigator information as designated by the NBDC.
- The information necessary to access the data is provided, and the data user can access the data.
5.4.3 Controlled-access Data
- The data user applies for data use in accordance with the procedure of application for data use. If multiple investigators from different organizations conduct a collaborative study, an application for data use must be submitted for each organization.
- After going through a review by the Ethical Review Committee of his/her affiliated or an equivalent organization with regard to the use of the NBDC Human Database and obtaining approval from the Ethical Review Committee, the data user submits, at the time of application for data use, a copy of a notification of permission obtained from the head of his/her affiliated organization. However, if the Ethical Review Committee decided to waive the review, the data user submits a document such as a notification of the fact.
- At the time of application for data use, the data user submits "Checklist for the NBDC Security Guidelines for Human Data" as well as other information and documents required by the NBDC Human Data Review Board.
- The NBDC Human Data Review Board decides whether access to the controlled-access data may be granted.
- After the NBDC Human Data Review Board approves the application for data use, the data user is granted access to the data and can access the data.
- In principle, the data user reports on data use status every year, using "Report on the Use of Controlled-access Data". In addition, at the time of reporting, the data user resubmits "Checklist for the NBDC Security Guidelines for Human Data".
- When the data user plans to distribute processed data with no or very low personal identifiability or primary data recoverability, the data user must apply to the NBDC Human Data Review Board Office using the "application for reporting on the completion of data use".
- When the data user needs to use the data set beyond the term originally stated in the application for data use, the data user may file an application with the NBDC Human Data Review Board Office, at least a month before the original expiration date, with a document such as the approval notification by the Ethical Review Committee of the affiliated organization or an equivalent organization (by which document the term approved can be confirmed) and a statement of desired term to be extended.
- When the data use is finished, the data user must promptly delete all data (whole data, or any part of the data stored. When the off-premise-server is used, all the data stored on the off-premise-server, including backup data on the off-premise-server.) and all data that can restore the data according to the NBDC Human Data Security Guidelines (for backup data on the off-premise-server, confirm when the data will be deleted) and report his/her data use (and deletion) to the NBDC Human Data Review Board Office, using the "application for reporting on the completion of data use". At the same time, the data user may apply for retention of secondary data (e.g., results of calculations based on controlled-access data) or distribution of processed data with no or very low personal identifiability or primary data recoverability by submitting "keep secondary data derived from controlled-access data" or "distributing processed data" in the "application for reporting on the completion of data use" to the NBDC Human Data Review Board Office, and may retain the secondary data. Depending on the degree of data processing and the storage period, however, the application may be rejected.
5.5 Cost of Data Use
The data user bears costs incurred in connection with data use, if any (e.g., in cases where data media are needed for sending data or where an ”off-premise-server” is used).
5.6 Termination of Data Use
- If the data user is suspected of a breach of any of the responsibilities listed in the section “5.3 Responsibilities of Data Users” or the NBDC Security Guidelines for Human Data, the NBDC investigates the matter. The NBDC Human Data Review Board makes a judgement on whether there was any misconduct, based on the result of the investigation, and if it is determined that misconduct occurred, the JST/NBDC:
- Orders the data user to stop using the data and revokes the permission to access the data set being used.
- Do not accept, for a certain period, a new application for data use from the data user who committed the misconduct. This period is determined by the NBDC Human Data Review Board.
- Report the misconduct to the head of the data user's affiliated organization, if necessary.
- In case the data in use are made unavailable due to a breach of the responsibilities of the data submitter, the data users may be requested to stop using the data. In that case, the data users are requested to follow the same procedure as those at the time of data use termination. Regardless of the reason, the NBDC shall not bear any responsibility for any damage or the like caused by the breach of responsibility of the data submitter.
6. Procedure for Revising the Guidelines
6.1 Proposal for Revision
Data submitters, data users, and potential users who are considering data use may propose revision of the Guidelines to the Office if they think it may lead to smoother provision or use of human data. It is requested to provide concrete proposals and references to the relevant parts of the Guidelines.
6.2 Review of Revision Proposals
Upon receipt of a revision proposal, the NBDC Data Sharing Subcommittee promptly reviews its content and decides whether the proposal is adopted or rejected or should be modified.
6.3 Announcement and Implementation of a Revision
Once the details of a revision are decided, they are promptly announced on our website and will be implemented after a certain period set by the NBDC Data Sharing Subcommittee. It should be noted that the revised Guidelines are also applied to those entities or persons who obtained approval for their application for data submission or data use before the implementation.
7. Other Topics
7.1 Disclosure of Information Obtained from applications for data submission and data use
From the applications received regarding the NBDC Human Database, the NBDC discloses some input items for which applicants' consent is obtained. The members of the NBDC Human Data Review Board and the staff of the NBDC Human Data Review Board Office must not disclose any other information on applications than the information disclosed by the NBDC to anyone other than those who are concerned.
7.2 Notification of Inaccurate Data
The NBDC Human Data Review Board accepts notifications about inaccurate data in the NBDC Human Database from data users and informs the relevant data submitters of the issue to discuss the response. Similar actions are taken in cases where people who gave consent point out a possibility of improperly obtained consent or fabricated consent.
Contact information: the NBDC Human Data Review Board Office
7.3 Investigation concerning Research Fraud by Fabrication or Falsification etc.
- The NBDC may cooperate on an investigation of research fraud regarding data stored in the NBDC Human Database, when requested.
- The head of the fraud investigation committee etc. should inform the NBDC of the Dataset ID of data necessary for conducting the verification and the necessity for verification, and report the security status of the server for storing the data using "Checklist for the NBDC Security Guidelines for Human Data".
- The Data should be used under full responsibility of the head of the fraud investigation committee etc.
- The head of the fraud investigation committee etc. should comply with rules under “Basic rules to be complied with in using data,” item (4) of “5.3.3 Controlled-access Data” in “5.3 Responsibilities of Data Users.”
See also:
NBDC Security Guidelines for Human Data (for Data Users) ver. 6.0
Click to Latest version.
April 1, 2022
Ver. 6.0
Introduction
The Department of NBDC Program (NBDC) of the Japan Science and Technology Agency operates the NBDC Human Database in accordance with the NBDC Guidelines for Human Data Sharing (hereinafter, the Data Sharing Guidelines). This “NBDC Security Guidelines for Human Data (for Data Users)” (hereinafter, the User Security Guidelines) provides the minimum set of requirements that should be fulfilled in order to safely utilize the registered-access data and controlled-access data defined in the Data Sharing Guidelines for the purpose of research activities, while protecting data confidentiality.
The controlled-access data may contain data that could be used to identify individuals in combination with other information. Therefore, measures must be implemented as required for the security level (standard-level (Type I) or high-level (Type II)) designated by a data submitter for each data set.
Because the information technology (IT) environments surrounding data users are diverse and ever-changing, merely complying with the User Security Guidelines may not be sufficient for data security. Data users are responsible for understanding their IT environments to be used for saving and calculating controlled-access data well, and taking additional security measures as deemed necessary, e.g., by referring to the security rules defined by the administrator of each IT environment as well as other guidelines[1][2].
The User Security Guidelines will be updated appropriately in response to IT developments.
1. Definitions
- Controlled-access data, Data
- The “controlled-access data” as defined in the Data Sharing Guidelines.
- Data accessible to registered users (Registered-access data)
- The “registered-access data” as defined in the Data Sharing Guidelines.
- Principal investigator (PI)
- The “PI” as defined in the Data Sharing Guidelines.
- Data user
- Data users who have been approved by the NBDC Human Data Review Board for the use of the controlled-access data, persons who have been entrusted by a data user to perform a work under the supervision of the data user, and data users of the registered-access data who have completed the registration for the use of the registered-access data.
- Data server (see Figure 1)
- A computer for data users to store and calculate controlled-access data, owned by the data user or the organization to which data users belong, or the “available server outside of affiliated organization (hereinafter, “off-premise-server”)” as defined in the Data Sharing Guidelines. In the IT environment including the data server, it is necessary to satisfy the following (1) to (4) as preconditions (except in the case of using only the off-premise-server).
- (1) Devices with high mobility, such as notebook PCs that are at high risk of loss or theft are not used.
- (2) The equipment of the data server and the storage device / medium storing the data are managed by the organization that owns them.
- (3) When installing the data server in a LAN, the LAN must be owned by the data users’ affiliated organization. In addition, on the LAN on which the data server is installed (hereinafter, data server-installed LAN), a firewall that restricts communication between the external network and the data server-installed LAN must be installed by the network administrator in the affiliated organization, and access from/to the outside is kept necessary minimal (Example: IP address and port of source and destination are limited) to maintain high security.
- (4) In the data server-installed LAN, if there is a computer used by a person other than the data users, the communication with other computers is appropriately managed by the firewall function.
- A computer for data users to store and calculate controlled-access data, owned by the data user or the organization to which data users belong, or the “available server outside of affiliated organization (hereinafter, “off-premise-server”)” as defined in the Data Sharing Guidelines. In the IT environment including the data server, it is necessary to satisfy the following (1) to (4) as preconditions (except in the case of using only the off-premise-server).
- Data access terminal (see Figure 1)
- A device that is for data users to access data in the data server and that does not permanently save the data locally. When transmitting data between the data access terminal and the data server, via a communication path outside the data server-installed LAN, it is necessary that all communication paths are encrypted with sufficient strength or that the data themselves are encrypted before being transmitted.
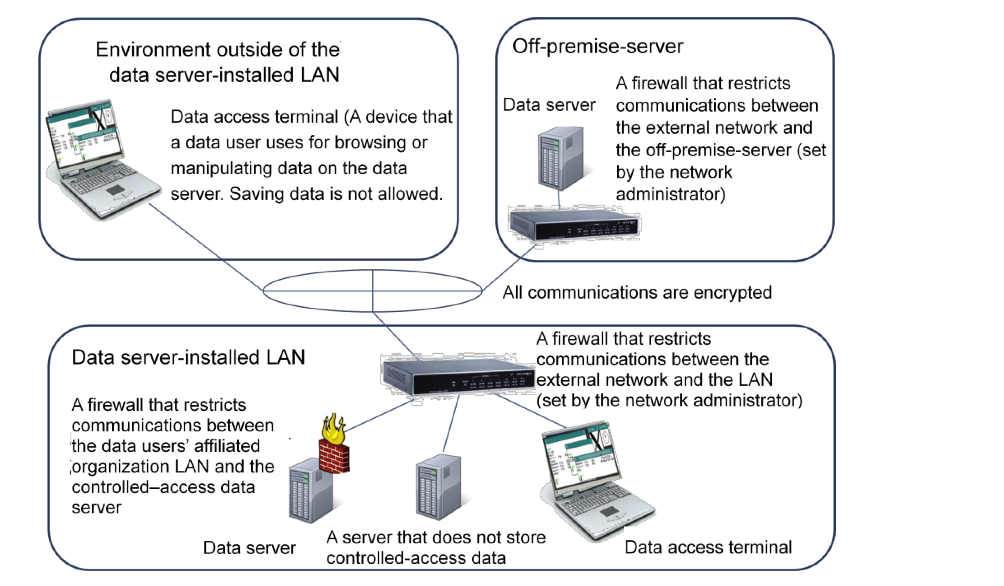
Figure 1 Data server-installed LAN, off-premise-server, data server and data access terminal
2. Measures to Be Taken under Standard-Level (Type I) Security
2.1 Basic Rules for Data Use
Data users must use the controlled-access data based on the following basic rules.
- Data users must store the controlled-access data in the data server and, in principle, must not move outside of the data server.
- In cases where it is unavoidable to temporarily move the controlled-access data outside of the data server but within the data server-installed LAN, data users must delete the data outside of the server promptly after use in a way that does not allow restoration.
- Data users must not duplicate data except for the following cases. In any case, however, duplicated data must be deleted promptly after use in a way that does not allow restoration.
- Creation of a backup copy of the data
- Temporary duplication for data transfer
- Temporary duplication performed by software
- Access to the controlled-access data is granted exclusively to the data users and must be conducted solely from data servers or data access terminals.
- Because IT environments surrounding data users are diverse and ever changing, data security is not necessarily guaranteed only by complying with these guidelines. Therefore, data users must understand the IT environment used for data storage and data calculation well, and take additional security measures as deemed necessary based on the security rules specified by the administrator of each IT environment and other guidelines[1][2].
2.2 What the Principal Investigator Must Do
Data use in general
- The PI should ensure that all data users fully understand and comply with the User Security Guidelines (For Data Users).
- The PI should confirm that the data users have received an education on information security implemented by their affiliated organization or the like.
- The PI should keep a record of information regarding data users and the data server (including information on the data storage place in the file system) in an electronic file or the like accessible to only data users, and update the record every time a change occurs. The record must be managed so that the update history can be reviewed.
- The PI should accept an audit conducted by the NBDC Human Data Review Board or a third party commissioned by the NBDC with regard to the state of implementation of security measures.
- The PI should submit "Checklist for the NBDC Security Guidelines for Human Data" to the NBDC Human Data Review Board Office at the time of application for data use and, in principle, every year thereafter.
- In case of a security incident such as data breach, the PI must follow the procedure described in “Responsibilities of Data Users” in the Data Sharing Guidelines and take measures such as notification to the NBDC.
Data server
When an “off-premise-server” is used, the PI must clarify the responsibility sharing with the “off-premise-server“ by means of the server usage rules etc.
- The PI should prepare for a data server (including a virtual server) and file system that are dedicated to the study as described in the Application Form for Data Use. When there is no choice but to use a server shared with other persons who are not data users, the access to the folders containing the controlled-access data should be limited only to the data users.
- If a computer used by a person other than data users exists within the data server-installed LAN, the PI should at least enable the firewall functions provided by the operating system (OS) (e.g., iptables in Linux) or equivalent to the function, and restrict communication from/to the inside of the data server-installed LAN properly.
- The PI should not allow sharing of a user ID or a password for the data server, even among data users. In addition, the PI must set a sufficiently strong password that cannot be guessed by others. (It must be at least 8 characters long. It is desirable to combine numbers, upper case letters, lower case letters and symbols. Do not use those that are easy to guess such as name, phone number, birthday, and the like.)
- The PI should apply the latest security patches insofar as possible for all software installed on the data server.
- The PI should not install unnecessary software, particularly, file sharing software (also called file exchange or P2P software; e.g., Winny, BitTorrent).
- The PI should install antivirus software, and perform virus scan at once whenever moving a file from the outside of the data server. The PI must keep the antivirus software and virus definition file up to date.
- The PI should not start unnecessary processes as many as possible when the OS boots up etc.
- Desirably, as security monitoring, the PI should periodically acquire and analyze various logs of the data server.
- When discarding a device that saved the controlled-access data, the PI should initialize the data storage or physically destroyed in a way that cannot be restored.
- In case of a security incident such as data breach, the PI should disconnect the relevant data server or data access terminal immediately from the data server-installed LAN.
2.3 What the Data User Must Do
Items 1. through 7. are to be complied with by data users of the registered-access data and data users of the controlled-access data, and items 8. through 13. are to be complied with only by data users of the controlled-access data.
- The data user should receive an education on information security implemented by the affiliated organization and the like and comply with the security rules set by the affiliated organization.
- The data user should not allow sharing of a user ID or a password for the data server, even among data users. In addition, the user must set a sufficiently strong password that cannot be guessed by others. (It must be at least 8 characters long. It is desirable to combine numbers, upper case letters, lower case letters, and symbols. Do not use those that are easy to guess such as name, phone number, birthday, and the like.)
- The data user should not access data from a terminal application on a device that can be used by many and unspecified persons (e.g., a PC in an Internet cafe).
- The data user should apply the latest security patches to the data access terminal whenever possible.
- When leaving a data access terminal, the data user should log out from the data server or lock the terminal. In addition, the terminal should be configured so that the screen is locked after a certain period of inactivity (around 15 minutes).
- The data user should disable a cache function, if any, which automatically saves data on the data access terminal.
- When it is inevitable to print data out (including the browse screen capture), the data user should strictly manage the printout to protect the confidentiality of the data, and shred the printout after use.
- When logging in to the data server from a data access terminal via computational network outside the data server-installed LAN, the data user should encrypt all the communication paths using a sufficiently strong encryption method every time data are transmitted between the data access terminal and the data server or encrypt the data themselves before transmitting them. It is desirable to perform similar encryption when logging in to the data server from the inside of the data server-installed LAN.
- The data user should not copy or save data displayed on a data access terminal screen to the local disk. It is desirable to use a data access terminal application that does not permit copying and saving of data displayed on the terminal screen to the local disk.
- When obtaining backup data, the data user should ensure that one of the following requirements is met:
- The backup is saved on the data server.
- When the backup is saved in a mobile device (e.g., a tape, USB memory, CD-ROM, notebook PC), the data is encrypted and deleted after use in a way that does not allow restoration. A record of information regarding the mobile device should be kept, e.g., in an electronic file accessible to only the data user, to minimize the risk of theft or loss and to enable early detection of an incident of data theft or data loss.
- When it is inevitable to use a mobile device for temporary data transfer, the data user should handle the data in the same way as backup data.
- After finishing data use, the data user should delete all data including all backups from all the devices in a way that does not allow restoration of the data. If the data cannot be deleted by the above method, such as for paper or a mobile device, the data should be physically destroyed in a way that cannot be restored by cutting or the like. It is preferable to delete any temporary file that was generated during computations as soon as it becomes unnecessary.
- In case of a security incident such as data breach, the data user should immediately disconnect the relevant data server or data access terminal from the data server-installed LAN and report the incident to the PI. In case where an “off-premise-server” is used, the data user should immediately take actions according to the off-premise-server usage measures etc.
3. Measures to Be Taken under High-Level (Type II) Security (except for using only an “off-premise-server”)
In addition to the measures listed in the previous section, “2. Measures to Be Taken under Standard-Level (Type I) Security,” the following measures must be taken with regard to the data server.
- The PI should place the data server in a server room that meets all of the following requirements.
- (1) Access to the room is limited, using multi-factor authentication with at least two of the following three authentication methods.
- Biometric authentication (e.g., vein, fingerprint, iris, and face recognition).
- Property-based authentication (e.g., IC card, one-time password, and USB token).
- Knowledge-based authentication (e.g., password).
- (2) Record of access to the room is automatically obtained and made available for later audit.
- (3) The server room must be dedicated to the purpose as described in the Application Form for Data Use. If a dedicated server room cannot be set up, the data server must be stored in a locked dedicated server rack.
- (1) Access to the room is limited, using multi-factor authentication with at least two of the following three authentication methods.
4. Contact Information for Inquiries about the User Security Guidelines
The NBDC Data Sharing Subcommittee Office
https://humandbs.biosciencedbc.jp/en/contact-us
References
[1] NCBI. NIH Security Best Practices for Controlled-Access Data Subject to the NIH Genomic Data Sharing (GDS) Policy. (Online) March 9, 2015.
https://www.ncbi.nlm.nih.gov/projects/gap/cgi-bin/GetPdf.cgi?document_name=dbgap_2b_security_procedures.pdf
[2] Ministry of Health, Labor, and Welfare. Iryojoho shisutemu no anzenkanri ni kansuru gaidorain (Guidelines for Security Management for Medical Information Systems) [in Japanese]. Version 5, May 2017.
http://www.mhlw.go.jp/file/05-Shingikai-12601000-Seisakutoukatsukan-Sanjikanshitsu_Shakaihoshoutantou/0000166260.pdf
Special Notes on Revisions
Amendments to Ver. 4.0
The wording has been rearranged and clarified, and changes to the procedures have been made to reflect the introduction of the new application system.
Amendments to Ver. 3.0
As a data server that uses controlled-access data, in addition to a server owned by the data users’ affiliated organization, the “off-premise-server” is made usable. Also, the security items are revised.
Amendments to Ver. 2.0
The term “Open data” in Ver. 2.0 is replaced by “unrestricted-access data” in Ver. 3.0.
Amendments to Ver. 1.0
In Ver. 1.0, Type II security required only biometric authentication; in Ver. 2.0, either property-based or knowledge-based authentication is additionally required even when biometric authentication is performed. If a room access control system has already been installed in accordance with Ver. 1.0, the system must be updated in compliance with Ver. 2.0 at an appropriate time (e.g., at the time of authentication device renewal or upgrade).

